¶ How to Resolve "DNS Rebind Attack has been detected" in OPNsense
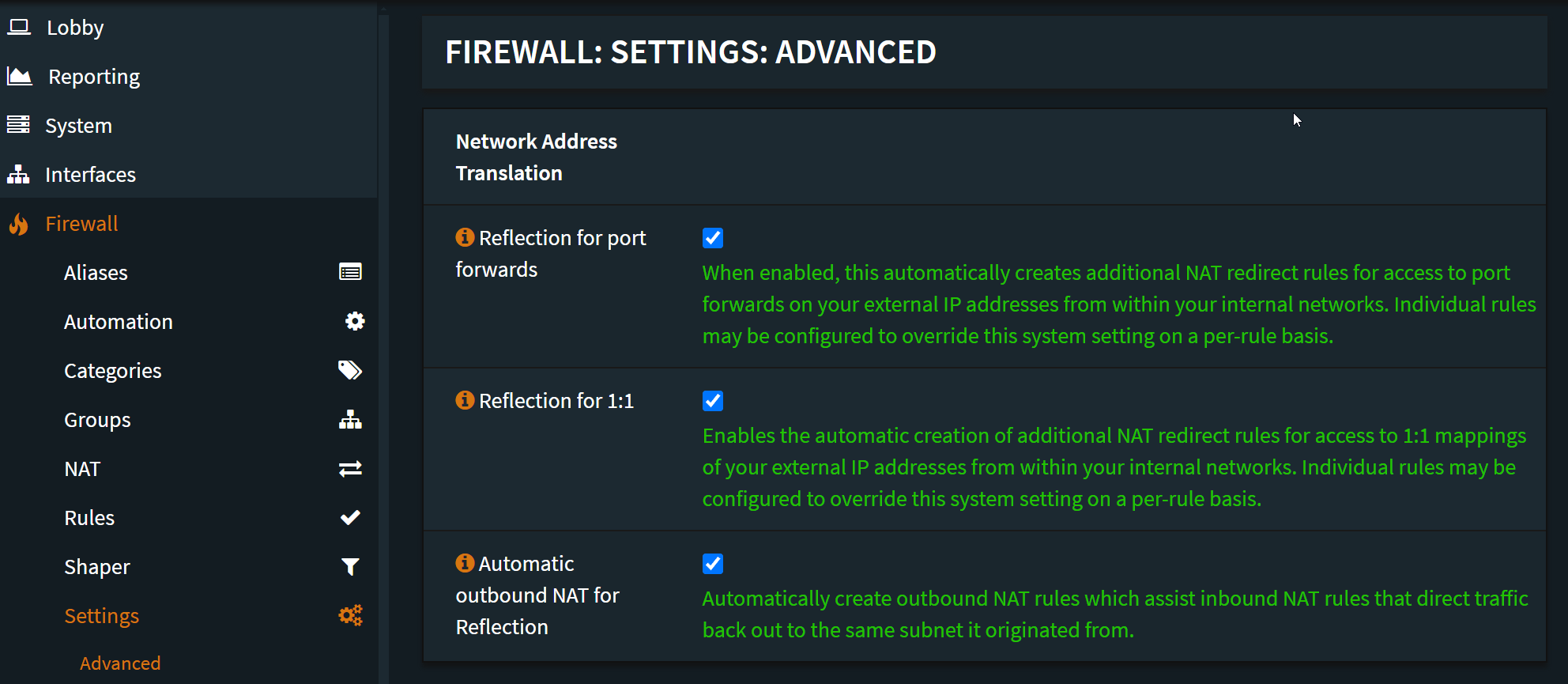
If you encounter the "DNS Rebind attack has been detected" error in OPNsense, one solution is to enable three specific options under Firewall: Settings: Advanced. These options help in managing how the firewall handles NAT reflection, which is crucial for services running on internal networks that need to be accessed via public DNS names.
Is possible that you have this iussue due to NPM Reverse proxy
¶ Enabling NAT Reflection Options
- Reflection for port forwards
- Reflection for 1:1
- Automatic outbound NAT for Reflection
¶ Detailed Explanation of Each Option
-
Reflection for port forwards:
- Purpose: This option creates additional NAT redirect rules for accessing port forwards on your external IP addresses from within your internal networks.
- Why Enable It: When this option is enabled, it allows devices on your internal network to reach public-facing services using the public DNS name. This can help avoid DNS Rebind errors by ensuring that the internal requests are properly redirected.
-
Reflection for 1:1:
- Purpose: This option enables the automatic creation of additional NAT redirect rules for access to 1:1 mappings of your external IP addresses from within your internal networks.
- Why Enable It: Enabling this option ensures that all 1:1 NAT mappings can be accessed from within the internal network using their external addresses. This is particularly useful for internal devices that need to access services using the same domain names as external clients.
-
Automatic outbound NAT for Reflection:
- Purpose: This option automatically creates outbound NAT rules which assist inbound NAT rules that direct traffic back out to the same subnet it originated from.
- Why Enable It: By enabling this, it ensures that the traffic reflection works seamlessly, supporting the other two options. It helps in maintaining proper routing of packets within the network, ensuring that internal devices can use public DNS names without running into issues.
¶ How to Enable These Options
- Navigate to Firewall > Settings > Advanced in the OPNsense GUI.
- Check the boxes for:
- Reflection for port forwards
- Reflection for 1:1
- Automatic outbound NAT for Reflection
- Save the configuration.
By enabling these three options, you can mitigate the "DNS Rebind attack has been detected" error, allowing internal network devices to access services using their public DNS names properly.
¶ Screenshot Reference
With these settings, your OPNsense configuration will support internal access to services using public DNS names, thereby resolving issues related to DNS Rebind protection.
¶ External References
For more detailed information, you can refer to the following external resources: